Fortress in the Cloud: How Security Zones Shield Your Data from Cyber Attacks
|
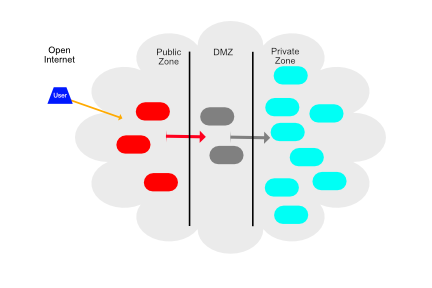
As modern applications grow more complex and valuable, their security becomes increasingly critical. Yet many organizations still operate with a flat security model—one breach and attackers gain access to everything. This approach is like building a house with a reinforced front door but paper-thin walls. How can you improve your application security to reduce your risk of attack? Use isolation zones. Isolation zones aren’t just a best practice—it’s the difference between a minor security incident and a catastrophic breach that makes headlines. How Do You Use Security Zones?When creating the production operational backend infrastructure for a modern application, it’s generally considered best practice for security purposes to split the application infrastructure into multiple security zones. This is so that a security breach in one area can still be limited to impact only the resources within that one zone. Done correctly, this can take a security breach that might otherwise be a massive impact on your application integrity and turn it into a much smaller, perhaps insignificant breach that has minimal impact. There are many ways to architect your security zones, but a typical model involves three standard zones. In this model, the three zones are called the public zone, the private zone, and the DMZ.
Security isolation isn’t just another checkbox on your compliance list—it’s a fundamental architectural decision that shapes your application’s resilience. Throughout my career, I’ve seen it over and over again. A proper zone implementation saves organizations from potentially devastating breaches. When attackers breach the public zone, they find themselves stranded, unable to reach the crown jewels in the private zone.
|